As companies enjoy the efficiency of digital Information Systems, their business rely more and more on the security of their networks and connected devices .
Don’t wait an incident to take action! Let Algen check your cyber-security!
A complete report will be handed to you, including:
- The list of the test performed
- The detailed vulnerabilities
- Recommendations to address the issues
- A global rating of the security of the infrastructure
Vulnerability Scanning
This is the step where hackers evaluate the opportunities available to them. To do so, the infrastructure is tested against a list of known vulnerabilities.
This step is made of 2 points:
- Over the internet. What can be exploited by a remote attacker ?
- On the local network. What are the possibilities for someone who infiltrated your network?
Wireless Exposure
WiFi technologies in the company is often a week point. Moreover, vendor-specific vulnerabilities can be discovered making WiFi a remarkable opportunity for people with bad intentions.
1 Minute, this is the approximate time to crack a weak WiFi encryption.
For better security, ask your infrastructure to be tested as soon as possible!
Website Security
Can your website be used to hurt your business?
WhiteHat Security revealed in their May 2013 report that:
- 86% of all websites had at least one serious vulnerability during 2012 that could lead to a takeover or information leakage.
- Serious vulnerabilities were resolved in an average of 193 days from first notification. Leaving 193 days when the vulnerability is known and documented, easily exploitable.
Get the condition of your website evaluated against threats now!
Network Visibility
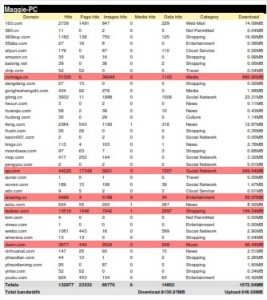
Get a detailed report of the threats and behaviors.
Algen will help you to have an insight in your network by helping you answering questions such as:
- Is there services running on my network that I am not aware of?
- Is internet a productivity or distraction tool?
- Is there dangerous behaviors among users?
- Are my data leaking outside the company?
- Can my colleagues read my emails?
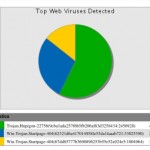
Who downloaded infected files?
Backups
Can your business be harmed by the loss of data? Well, the answer seem obvious, as most companies are relying on the availability of their data.
Algen will assist you in making sure that your productivity will survive the loss of a computer, server or even your entire IT infrastructure!
Training
All security systems have weaknesses and most of the time the most obvious one is Humans!
The easiest way to steal information is to politely ask for it!
Information about risky behaviors is actually one of your first line of defense. As pointed by the BestVPNService survey, 77% of victims of cyber crimes connected to free open WiFi which is known to be dangerous when not aware of the risks.
In a 1 day training, Algen security team teaches the most common traps used to get in an information system. Among the topics:
- Social Engineering
- Identity theft
- Phishing emails
- Safer web browsing
- Mobile security
- Password management
- General good practices
Take action now by Contacting Us!



